Vulnerability Assessment is the initial step in identifying weaknesses within a computer system, network, or application. It involves a systematic approach to scanning and analyzing various components to uncover potential vulnerabilities that could be exploited by attackers. The primary goal of VA is to identify and categorize vulnerabilities based on their severity and potential impact on the organization’s security posture.
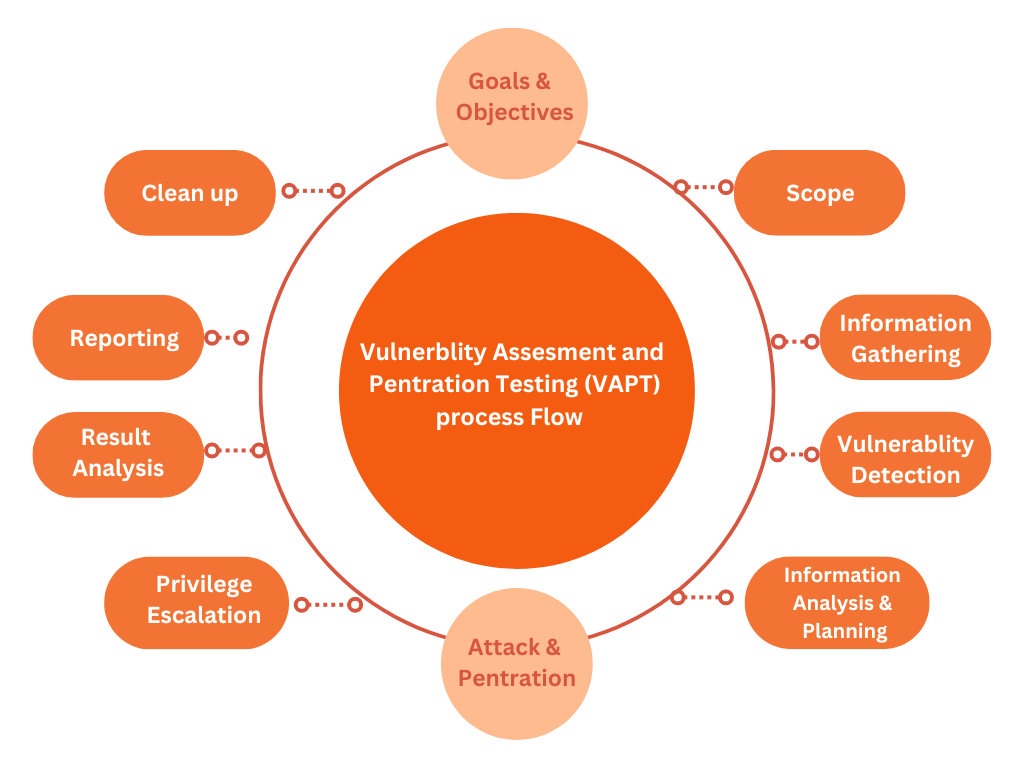
Penetration Testing takes the assessment process a step further by simulating real-world attacks on an organization’s systems and infrastructure. Unlike vulnerability assessment, penetration testing involves active exploitation of identified vulnerabilities to determine the extent to which an attacker can gain unauthorized access or compromise sensitive information. Skilled ethical hackers, often referred to as penetration testers or “red teamers,” perform these tests to assess the security of the organization’s defenses.
Vulnerability Assessment is the initial step in identifying weaknesses within a computer system, network, or application. It involves a systematic approach to scanning and analyzing various components to uncover potential vulnerabilities that could be exploited by attackers. The primary goal of VA is to identify and categorize vulnerabilities based on their severity and potential impact on the organization’s security posture.
Vulnerability Assessment and Penetration Testing are essential components of cybersecurity that together provide a holistic approach to identifying, addressing, and mitigating potential security risks. By systematically assessing vulnerabilities and simulating real-world attacks, organizations can enhance their security posture and safeguard their digital assets from cyber threats.

Call us any time:
+91 9106147779Email us 24/7 hours:
shifa@hacktify.inCopyright © 2023 Hacktify All Rights Reserved.
WhatsApp us